Scrunch: Rewriting the Web for AI


Today, we are incredibly excited to announce our investment in Nebulock, an agentic threat hunting platform. In the AI era, attackers use AI to move fast, generating polymorphic malware, automating lateral movement, and evading traditional detections. Meanwhile, most defenders are stuck reacting to noisy alerts and brittle detection rules.
Nebulock flips the script. It delivers always-on, autonomous threat hunting that surfaces real findings across EDR, identity, and cloud telemetry, before an alert ever fires. The company was founded by Damien Lewke, who formerly led product for Arctic Wolf and Crowdstrike. We sat down with Damien to talk to him about his vision for Nebulock in our founder Q&A:
I was born in Greenwich, Connecticut but moved to Frankfurt when I was just a few months old. My dad was an executive recruiter, and his firm needed someone in Germany. So I grew up speaking German at home, watching Bundesliga, and learning to see the world as much larger than wherever you happen to live.
My childhood was centered around endurance athletics. I ran. I biked. I swam. I did my first triathlon when I was nine years old. Saturday mornings were spent on long-distance runs and bike rides with my dad. We’d do 60-80 mile rides on a regular basis which was our favorite way to spend time together. In high school, my world revolved around soccer. I fell in love with the game by accident—I signed up just to get out of the swim team. But the first time I touched the ball in a game, I scored a goal. I was hooked.

Following that experience, I trained relentlessly. Played for club teams, school teams, and rec teams. Practiced free kicks after dark. At fifteen, I was recruited to play on a professional team in Germany which was rather atypical for an American at the time. I moved back, this time alone, to chase the pro dream. I will never forget playing for Quelle Fuerth in the Bayernliga, and living a life trying to perfect my craft as a professional footballer.
Looking back, those years away from home, training taught me a lot about rhythm, discipline, and suffering. Not in a negative way—just the reality that if you keep moving forward relentlessly, eventually you arrive somewhere. That mindset has shaped how I approach almost everything.
In college, I became obsessed with adversarial game theory. It started as an intellectual curiosity: how do you make decisions when you're operating under uncertainty, and the other side is actively trying to outsmart you? I loved the idea of asynchronous conflict. It felt real, like something you could apply beyond the classroom. That line of thinking led me into the world of defense and right out of school I joined Northrup Grumman, the large defense contractor. There, I joined the team that worked on the contract on the nuclear modernization program which required DoD Top security clearance, a really exciting prospect for a fresh grad. My job was to threat model the entire system from beginning to end. And I don’t mean just the software—I mean the physical supply chain, the comms infrastructure, and all the analog-to-digital transitions across the stack. That was the first time I saw cybersecurity not just as a technical problem, but as a strategic one. It wasn’t about patching CVEs. It was about modeling how people think, how systems break, and how to harden an entire architecture against malicious intent.
In 2016, I read about Crowdstrike’s involvement in the DNC hack. I thought, “These are the people solving the hard problems.” So I made it my mission to join the company when it was roughly 200 employees.

I wore a lot of different hats from marketing, product, sales and solutions engineering but primarily worked on helping build and launching Falcon Complete, Discover, Spotlight and our partnership with Dell, including building deep integrations with Dell and VMware to deliver Falcon to millions of endpoints via OEMs. When I joined we were just crossing $25M in ARR. By the time I left, we’d gone public.
At Northrop, I saw firsthand how aging systems, built decades ago, riddled with legacy gaps, could still be modeled, hardened, and defended if you understood their underlying structure. At CrowdStrike, I saw the other end of the spectrum: what it looks like when a company hits true product-market fit and scales with speed and precision. I helped launch products and build out OEM integrations with, watching the company go from scrappy to IPO in just a few years.
But one thing never changed: the hardest, most important part of defense, threat hunting, was still largely manual, brittle, and single-threaded. Even at Arctic Wolf, where I led product for AI and threat intel across a thousand-person SOC, our best analysts were still spending their time chasing alerts, revalidating detections, and rewriting the same logic over and over.
That pain became personal. I’d been the one up at 2 a.m., replaying logs, trying to piece together a lateral movement path. I knew the workflows were broken and I knew AI could help, if you gave it the right frame.
When I eventually attended MIT’s Computer Science & AI Lab (CSAIL) for my graduate degree, I finally had space to explore that frame. I was surrounded by people who weren’t just talking about machine learning, they were pushing the frontier of what AI could actually do in real-world systems. I became fascinated with how deep learning could reason over large, noisy data sets, especially telemetry, and simulate the kind of hypothesis generation that threat hunters do instinctively. That’s when it clicked: what if we could build a system that hunted like a human, but never slept, never got tired, and got better with every iteration?
That idea became Nebulock. A platform that moves the industry beyond passive alerting but rather toward true, proactive detection. Something that learns your environment, writes detections, adapts to drift, and gets smarter every time it hunts. That’s what I wanted as a practitioner. So that’s what we’re building.
Because attackers have already made the leap. Nation-state groups like Volt Typhoon spent nearly a year inside U.S. infrastructure. Then Cyber Av3ngers came along and replicated the same behavior, in days, using AI. They moved faster, pivoted smarter, and operated with surgical efficiency.
Meanwhile, defenders are still doing quarterly threat hunts by hand. Still relying on a single analyst to write the right query. Still hoping they see the breadcrumb in the logs. Agentic threat hunting flips that script. It means the machine hunts continuously. It forms hypotheses. It explores paths. It adapts based on what it finds.
This isn’t about replacing humans. It’s about giving them a system that can keep up. A system that thinks like a threat hunter, scales like a cloud platform, and improves with every iteration.
Our vision is to make elite autonomous threat hunting available to all enterprises, not just those who can afford it or have the requisite talent in-house. That means three things. As new threats emerge and embed themselves into enterprise infrastructure, we want to harden it by threat hunting on each attack surface 24/7.
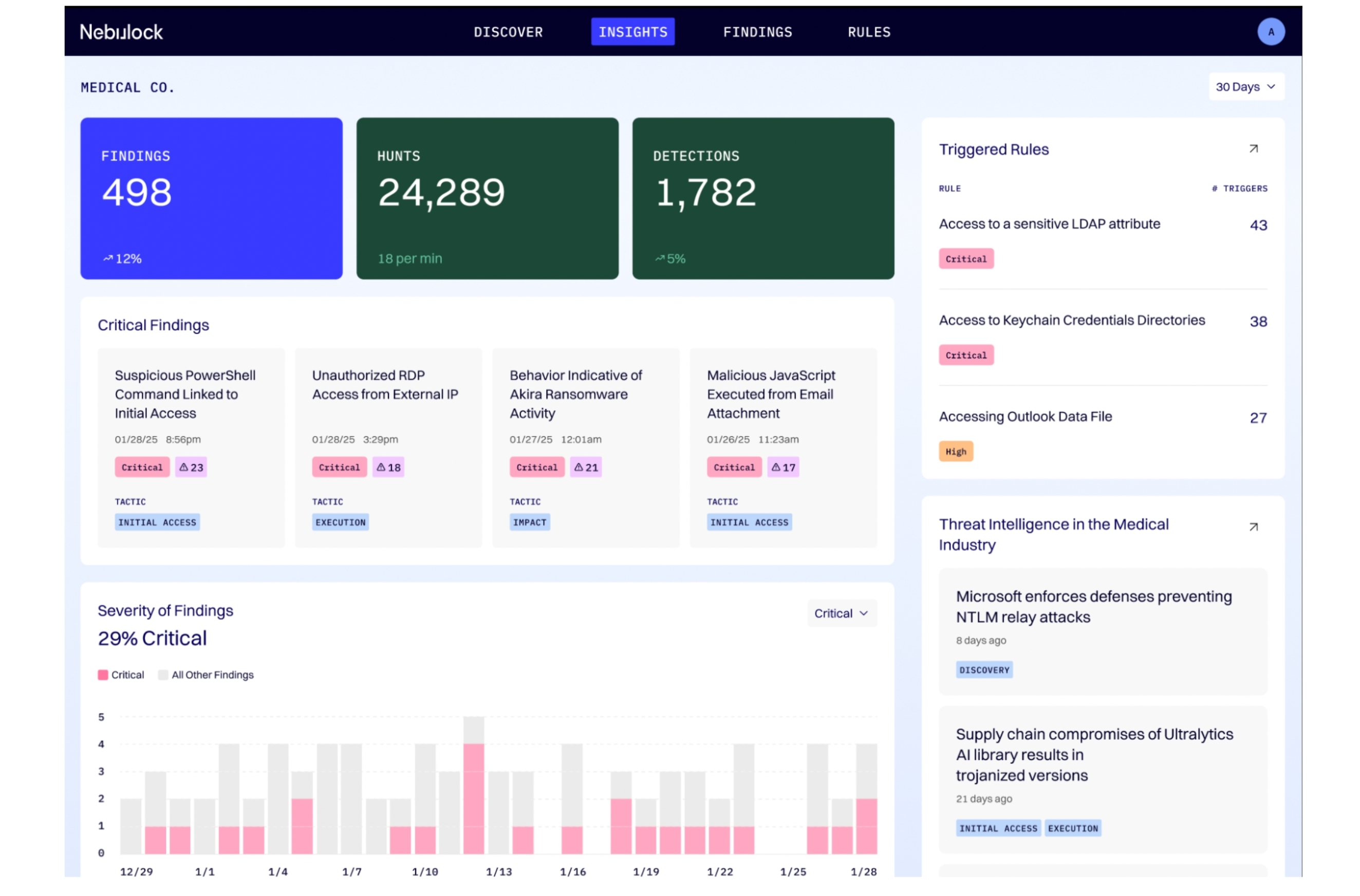
Continuous Threat Hunting:Nebulock connects to your identity, endpoint, and cloud telemetry and hunts 24/7—no playbooks required, no human prompting needed. It thinks on its own and surfaces real anomalies before attackers can entrench.
Drift-Aware Detection Engineering:When we find something, we don’t stop at alerts. Nebulock builds detections, tests them against your environment, checks for logic drift, and rewrites or improves them automatically. You can review it—or you can let us deploy.
Focus on Behavior, Not Just Signatures:Most serious breaches aren’t about a signature. They’re behavioral. Someone uses a stolen credential, moves laterally, blends in. Nebulock finds the deviations, connects the dots, and raises the signal long before a ransomware detonation.
In the background, we’re building a simulation engine. One that uses synthetic data and reinforcement learning to test detections before they ship. So when we tell you a threat is real, we’ve already seen it play out. Long-term, we want Nebulock to be your friendly neighborhood threat hunter, the one who never sleeps, never forgets, and never stops hunting.
